
SSL Enforcer
SSL Enforcer - Force SSL/TLS encryption for any browser or app. Block all unsecure connections.
Documentation
Today a vast majority of Internet activities like social networking, streaming videos, messaging are based on HTTP protocol. Unfortunately, it does not provide encryption by default so your data including sensitive details like passwords, private information, etc can be intercepted. This can also compromise your privacy because your activities can be tracked by a third party.
All these problems can be addressed by HTTPS protocol that provides encryption based on SSL/TLS secure connection. The number of resources that are available through HTTPS is constantly growing but it will take a long time until unsecure HTTP becomes obsolete and disabled by default.
Since both protocols coexist, it is hard to make sure that all connections go through secure SSL/TLS channels. Modern Internet applications provide little control over this. No options exist on the operating system level as well.
SSL Enforcer solves this problem and provides you with a flexible control over HTTP/HTTPS connections. Depending on your scenario, it can block all unsecure HTTP connections, check for secure alternatives and redirect the connections accordingly. The processing takes place on the system level, so it ensures no data leaks. It is fully transparent for user applications.
In the best-effort mode, SSL Enforcer redirects to HTTPS only when it is available on the server. Connection check happens in the background so there is no interruption for the user application. Thus you automatically get the best available security while your user experience remains unaffected.
SSL Enforcer can also control SSL/TLS versions and cipher suites for all connections including non-HTTP protocols like the ones used in email and other applications. It can block insecure outdated SSL/TLS versions.
SSL Enforcer is available as a download package at www.sslenforcer.com web site. It can be installed on Microsoft Windows 7, 8, 8.1, 10 (32- or 64-bit editions) and Apple Mac OS X 10.6-10.10.
On Windows, run SSLEnforcerSetup.exe setup program and follow the steps of installation wizard.
On Mac, unzip and copy SSL Enforcer.app to /Application folder on your Mac.
You can uninstall SSL Enforcer at any given time.
On Windows, use Start‑>SSL Enforcer‑>Uninstall SSL Enforcer program or Windows Control Panel.
On Mac, move SSL Enforcer.app to Trash.
Either of these actions will completely remove SSL Enforcer from your system.
When you start SSL Enforcer, it runs at the background and adds its icon to the system tray on Windows or menu bar on Mac.
Microsoft Windows
Mac OS X
To open main window, click this icon (Microsoft Windows). Or right-click the icon and select Preferences from the menu (Mac OS X).
By default, SSL Enforcer intercepts all unsecure HTTP connections that go to the predefined ports 80, 88, 3128, 8080-8088 for all applications (you can change this at Options). In the same time, it checks for HTTPS availability and redirects the connection automatically if possible. Cache is used to speed-up the process.
In Best-Effort Mode (default), if HTTPS is not available for the requested resource, the connection will be opened as is.
In Strict Mode, the connection will be blocked and your browser will display the following page. Here you can get a detailed information about the problem and add the target to the exclusion list.
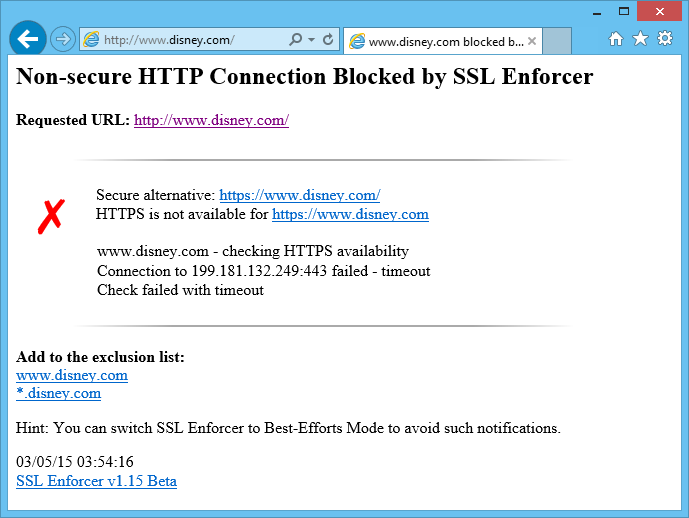
HTTPS is not available for www.disney.com
In the main window, you can change any settings on the fly. Additional options are available through Options... button. Show Log... opens the log window. Use On/Off toggle to enable/disable SSL Enforcer.
To quit the program, right-click on the SSL Enforcer icon and select Exit from the context menu.
To open the main window, use SSL Enforcer system tray icon. The window contains all main controls of the program. All changes to these settings will be effective immediately. There is no need to restart SSL Enforcer.
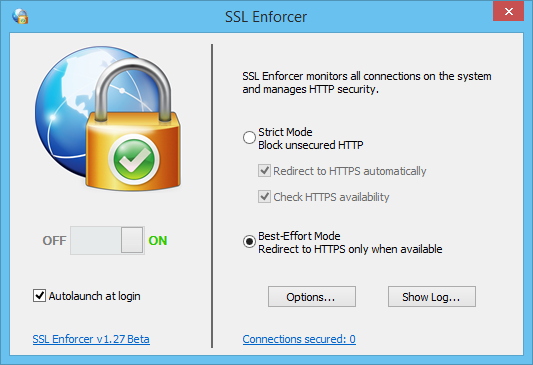
SSL Enforcer main window
On/Off toggle allows you to enable/disable SSL Enforcer without quitting the program.
Autolaunch at login starts SSL Enforcer automatically on Windows startup (user login).
Options... button opens a window with additional options.
Show Log... button shows the log window where you can monitor for the network events in real time.
Some of the controls are also available through the context menu that can be opened by a right-click on the system tray icon.
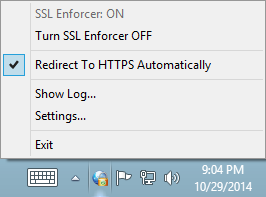
System tray context menu
In the main window you can switch between two distinct working modes – Strict Mode and Best-Effort Mode.
Strict Mode
When this mode is enabled, SSL Enforcer blocks all unsecured HTTP connections (subject to the exclusions set at Options). This provides the best security and ensures no data leaks over unencrypted channel.
Additionally, you can make SSL Enforcer to Check HTTPS availability for the requested resource. The check involves comprehensive test of SSL/TLS connection, alternative hostnames (with and without "www" prefix), dead loop redirects, etc. Check results for each host are cached to avoid multiple checks of the same resource.
In case of a problem, the result of the check will be printed in the browser and the log.
In many scenarios, it is convenient to Redirect to HTTPS automatically. If this option is enabled and HTTPS is available for the resource, your work will not be interrupted as the redirection is transparent for the user applications like browser. If this option is not set, SSL Enforcer generates a error page in your browser.
Best-Effort Mode
In this mode, SSL Enforcer redirects to HTTPS only when it is available for the requested resource. All processing including the check, waiting and redirect (if possible) is transparent for the user application. This allows you to add more security for all your Internet activities. SSL Enforcer will ensure that your data travels through encrypted channels whenever is available. In the same time, you can still access resources that do not support HTTPS.
The only drawback is some additional delay needed for SSL/TLS check. Although this is an issue only when the host is requested for the first time. After that, the results will be instantly retrieved from SSL Enforcer cache.
Another problem is that some hosts may have SSL/TLS available while the web site is not properly configured for HTTPS. Such hosts should be added to the exception list.
Options window is available through the click on the Options... button at the main window. It allows you to fine-tuning SSL Enforcer. The changes to the settings will be activated upon the click on OK button.
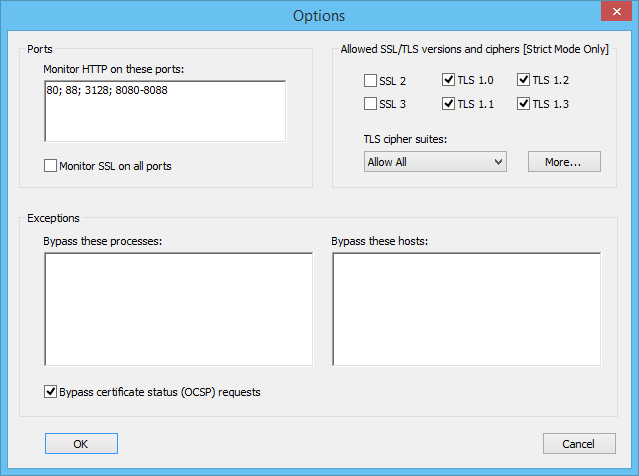
Options window
Ports
This field allows you to specify the list of the TCP ports that SSL Enforcer monitors for HTTP connections. Use semicolon (;) to separate particular ports or port ranges.
Example: 80; 88; 3128; 8080-8088;
Monitor SSL on all ports
Enable this option if you wish that SSL Enforcer controls SSL/TLS versions and cipher suites on all ports. By default, it monitors port 443 only.
Allowed SSL/TLS versions and ciphers
Select SSL and TLS versions that you wish to allow. Unselected ones will be blocked.
You can allow TLS cipher suites from the predefined list: All, Safe Only, Safe Only with Forward Secrecy.
Use More... button to customize the list.
Process Exceptions
Add process names here that you do not want to be handled by SSL Enforcer. All connections of such processes will completely bypass SSL Enforcer. Use semicolon (;) as a separator. Omit the path. If the name contains spaces, wrap the name in double-quotes (").
Example: example.exe; "long name app.exe";
You can add or remove a process from the list if you click on it at the Log window.
Host Exceptions
Add host names here that you do not want to be handled by SSL Enforcer. All connections to these hosts will completely bypass SSL Enforcer. Use semicolon (;) as a separator. Wildcards (masks) are supported.
Example: microsoft.com; *.example.net
You can add or remove a host from the list if you click on it at the Log window or through web page generated by SSL Enforcer.
Bypass certificate status (OCSP) requests
When working with HTTPS some browsers try to validate SSL certificates through OCSP protocol. This is done to make sure that SSL certificate is still active and it is not revoked. The validation itself works through HTTP thus SSL Enforcer may prevent this connection.
Since there is no user data leak during OCSP validation; it makes sense to keep this option enabled. This way SSL Enforcer will bypass OCSP requests so they will work as intended.
You can customize allowed TLS Cipher Suites with More... button from the Options window.
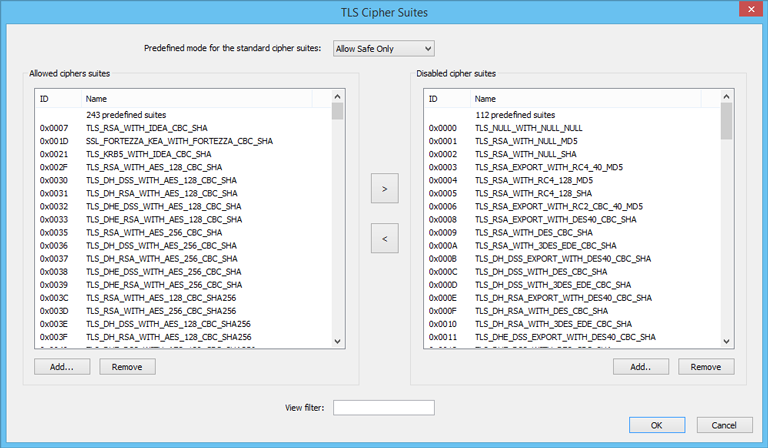
TLS Cipher Suites window
The window contains two lists of cipher suites. The left list is for allowed suites. The right list is for disallowed ones. You can switch between predefined modes at the top of the windows that will populate both lists accordingly. There are three modes available: Allow All, Allow Safe Only, Allow Safe Only with Forward Secrecy.
Use arrow buttons to move a cipher suite between the lists. This enables or disables the suite. With Add.. or Remove buttons you can add or delete a user-defined cipher suite. This is useful for proprietary or new ciphers.
View filter allows you to quickly find cipher suites. For example, you can type “DES” to output the only cipher suites that contain this term.
To open the log window click Show Log... button at the main window. SSL Enforcer outputs all network events to the log. It provides you with a detailed information about all SSL Enforcer activities.
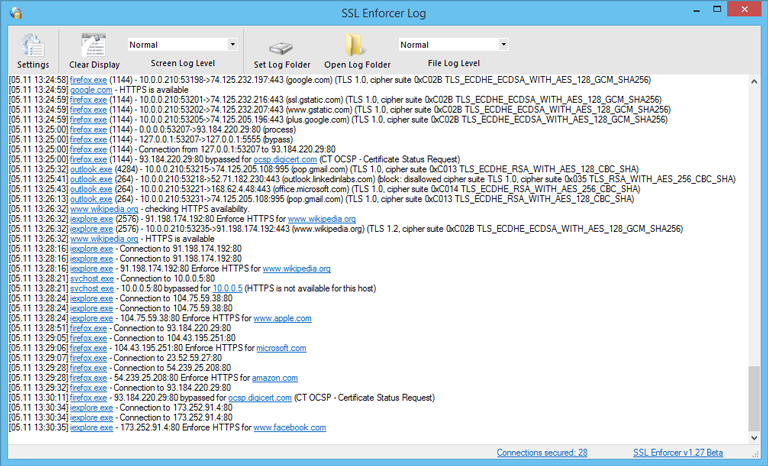
Log window
If you click on the highlighted item (process or host), you can add or remove it from the exclusion list that is also available at the Options.
You can change the verbosity of the output through Screen Log Level control. In Verbose mode, SSL Enforcer outputs all events including information about connections that are not processed. Additionally, it outputs SSL/TLS version and cipher suite. This can be helpful for troubleshooting. Error messages are marked in red. Use Clear Display to clear the output.
You can also make SSL Enforcer to write file log. To do this, set File Log Level to desired verbosity. To disable the log, set File Log Level to None. Use Set Log Folder and Open Log Folder to manage the log file.
Settings will bring you to the main window of SSL Enforcer.
For each HTTP host SSL Enforcer performs a comprehensive check for HTTPS availability. It includes a number of tests and can take up to 10 seconds. The result of the check for each particular host is cached. Next time when the same host is requested, SSL Enforcer uses a previous result from the cache. When the cache is outdated, the check is performed again.
To preserve the cache across a restart the following file is used:
C:\Users\<Username>\Documents\SSL Enforcer\https_cache.xml
You can manually edit the cache file while SSL Enforcer is not running.